HTTPS: Encryption on the Web
In most cases where a web browser or app on a mobile phone is used to surf on the Internet, encrypted connections are used through an HTTPS communication protocol (HyperText Transfer Protocol Secure or HTTP on TLS). This technique was initially applied to ensure communications in payment methods and online banking. Today, most websites use HTTPS by default and it has become an essential tool for privacy, as it allows for the encryption of communications from end to end, that is, between the two parties who communicate with one another.

HTTP (Hypertext Transfer Protocol) is the protocol used on the Internet for communications between browsers or Apps and web servers. Created in the 90’s and updated in 2000, its original setting did not include measures ensuring confidentiality of communication, just like all protocols created at the time. One way to solve this need is through the VPN technology (Virtual Private Network), which makes it possible to tunnel and encrypt these unsafe protocols through third-party tools.
An HTTP update, published in 2015 and known as HTTP2, did have end-to-end communication encryption, but only as an option. The HTTP3 version, recently published, includes, among other improvements, the encryption of communications as a compulsory measure. For the time being, it only has a use of 7% on the Internet, but a fast adoption of this protocol is expected, as it will contribute to privacy on the Internet in a positive manner.
Concurrently to the evolution of the HTTP and in order to solve the original deficiencies in the HTTP, the company Netscape developed the SSL protocol (Secure Socket Layer), an addition to work with HTTP that makes it possible to perform the encryption of the information transferred, thus ensuring both integrity and confidentiality.
Adopted as a de facto standard in the encryption of communications on the Internet through an integration with HTTP, SSL has become to be known as TLS (Transport Layer Security). TLS 1.0 was implemented in 1999 and has since then experienced several updates so as to overcome the different security problems. Today, it has reached the TLS1.3 version, which is the standard used by the new HTTP3 version.
The applications of HTTP to TLS, or to HTTPS, provide confidentiality and integrity in communications, as well as authenticity in the sense that we can confirm that we are accessing the server written in the address bar of the browser. Notwithstanding, we must not forget that there are attacks such as phishing. Such attacks include a link that redirects to a fraudulent domain with a deceiving address, even with a valid certificate for that domain. These attacks seek to obtain personal data for non-legitimate purposes by forging the website of the legitimate organisation.
In order to ensure compatibility with non-updated tools, websites usually enable connections with protocols that do not add the suitable guarantees. Cybersecurity bodies advise against the use of versions older than TLS1.2 for considering them insecure. Administrators of websites will need to set the servers so that they only accept the last TLS versions. In addition, it is also advisable to perform verifications of TLS vulnerabilities. To that end, users may use tools, either online or installable at a local level, such as testssl.sh that make it possible to audit the security of our server with regard to the use of HTTPS.
Users can ensure they are not using insecure protocols in our browsers. Below, several setting instructions are given for the most frequent browsers:
Chrome/Edge
For Chrome/Edge, in Internet Settings, in advanced settings, untick the older versions.
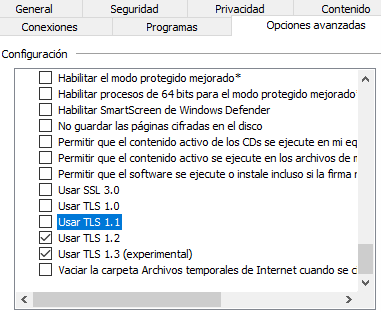
Firefox
On firefox by writing about:config, search tls (3 refers to TLS1.2 and 4 refers to TLS1.3)
![]()
With these settings access is avoided to a webpage with encryption versions that do not provide the same level of security to our communications as TLS 1.2 or TLS 1.3.
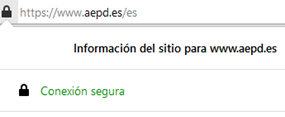
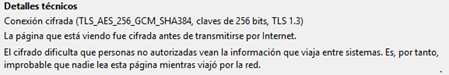
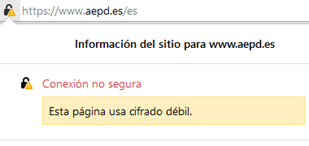
Today, most browsers warn the user when a connection is being used that is considered insecure. For example, see the comparison in the following figures between the warning of the browser at the time to use TLS 1.3 (secure) or TLS 1.0 (insecure).
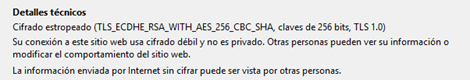
You may find further information on the Innovation and Technology website of this Agency, as well as on our blog:


