Phishing Campaigns Regarding The Coronavirus
The alert situation caused by the coronavirus at a global level is a dangerous breeding ground for phishing attacks, which are being carried out internationally through instant messaging services, e-mail and any social media. Cybercriminals always try to take advantage of situations of fear and panic, and the current situation is no exception.
The alert situation caused by the coronavirus at a global level is a dangerous breeding ground for phishing attacks, which are being carried out internationally through instant messaging services, e-mail and any social media. Cybercriminals always try to take advantage of situations of fear and panic, and the current situation is no exception.
While the state of alert caused by the new coronavirus lasts, cybercriminals will seize the opportunity to launch phishing attacks and all sorts of actions to take advantage of these moments when we are overflowing with information and thus particularly vulnerable.
The modus operandi is always very similar: cybercriminals will try to supplant legitimate organisations with relevant information about the coronavirus, such as the Ministry of Health, the Department of Health of an Autonomous Region, law enforcement agencies, international organisations or even the company you work for. They will do this via instant messaging services like WhatsApp or Telegram, and also via e-mail. In most cases you will be asked to urgently open a file or follow an internet link in order to obtain the information.
If you follow the link and download and execute an attachment, it will be some sort of malware that allows cybercriminals to take control of your device, access your information and personal data, and even encrypt said data.
Internet links included in these messages or e-mails may also lead you to websites that supplant other organisations and steal your service access details or other personal information, such as your social security number, bank details for payment of a coronavirus test, etc. See examples in figures 1, 2 and 3.
You can obtain further information about these and other threats in the Guide to Privacy and Security on the Internet published by the AEPD.
Follow the recommendations below:
• Stay informed through official and reliable sources by accessing directly the websites of the institutions or social media, never through links provided in a message or an e-mail.
• Verify the e-mail address sending the message and also the web link provided in the message. Sometimes it is obvious that the web address is not legitimate, but cybercriminals are also able to create links that are very similar to legitimate addresses.
• Be careful with requests for personal data via websites accessed by following a link contained in an e-mail or message. The best option is to go directly to that organisation's website and verify that the service is original.
• Pay attention to the content of the message: you should be suspicious of messages with spelling mistakes, grammatical errors and generic greetings that do not provide any personal data, such as "Dear citizen" or "Dear patient".
• Be much more suspicious if the content of the message also urges you to take any action as soon as possible, with unjustified urgency.
If, even following these recommendations, you fall into their trap, remain calm and contact the Internet User Security Office, which reports to the INCIBE, in order to obtain advice on how to act to minimise potential damage.
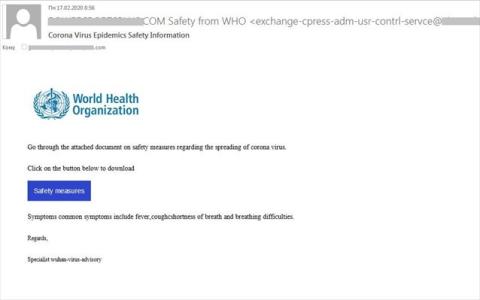
Figure 1. E-mail impersonating the WHO with a malicious link to protection measures.
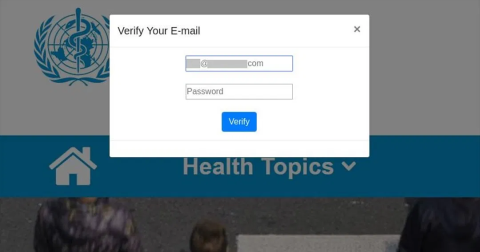
Figure 2. Following the link of the example in figure 1, you are asked to verify your e-mail for information, and they seize the opportunity to steal your credentials
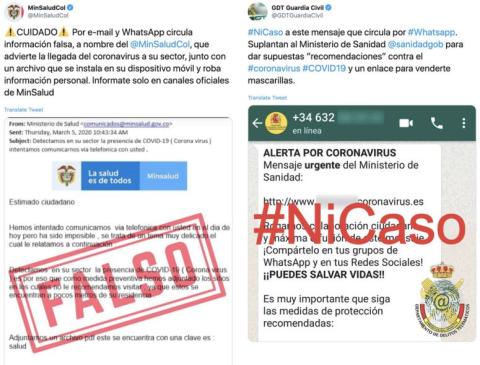
Figure 3. Examples of phishing attempts in Spain.


